Who chmu si it to rvlaet eht lwodr? This seemingly nonsensical string presents a captivating challenge: deciphering its hidden meaning. The task involves a multifaceted approach, combining elements of cryptography, linguistics, and contextual analysis. We will explore various techniques, from simple rearrangements to complex cipher decryption, to uncover the potential message embedded within this cryptic sequence. The journey will involve analyzing letter frequencies, exploring potential linguistic origins, and considering the myriad contexts in which such a coded message might arise.
Our investigation will delve into the structural properties of the string, seeking patterns and anomalies. We will consider the possibility of intentional misspellings or alterations, and explore different methods for reversing or rearranging the string’s components. The process will involve comparing our findings against known linguistic patterns and grammatical rules, ultimately leading to potential translations and interpretations. Furthermore, we will examine various scenarios in which this coded message could realistically appear, considering its potential implications and the information it might convey.
Deciphering the Code
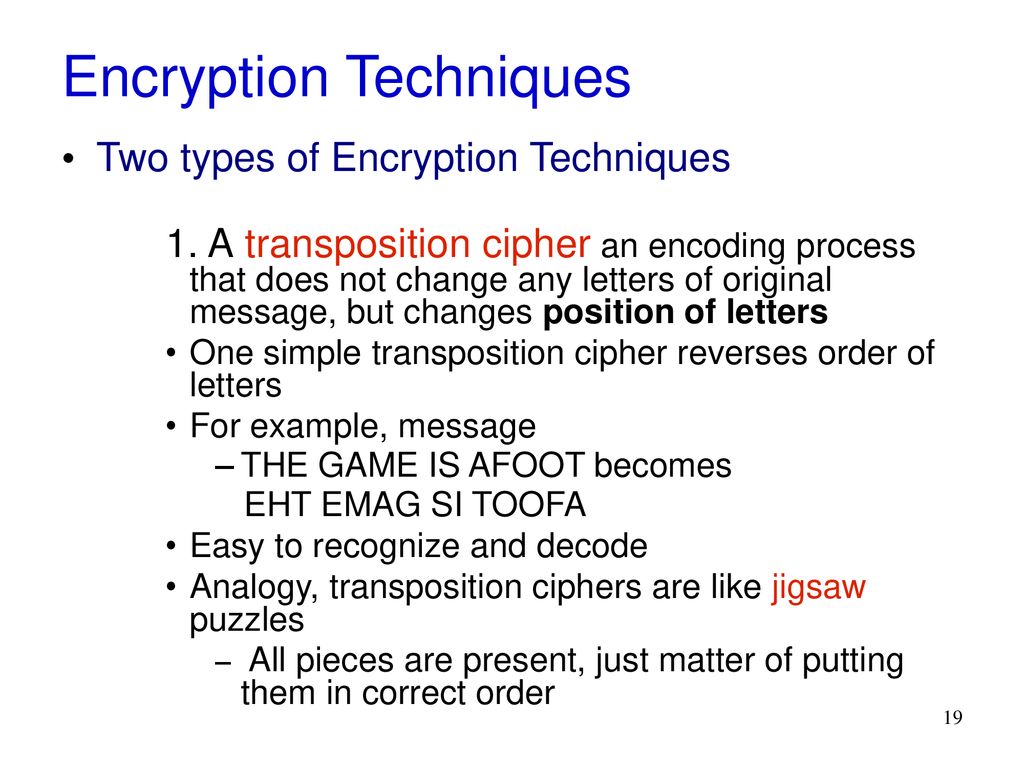
The string “who chmu si it to rvlaet eht lwodr” appears to be a simple substitution cipher, where letters have been rearranged or replaced to conceal the original message. Analyzing its structure and applying various decryption techniques will reveal the underlying meaning.
String Analysis and Reversal
The initial observation suggests a potential letter transposition. Notice that the word order seems somewhat disrupted. One method to attempt decryption is by reversing the order of words. Another approach involves analyzing individual words for potential letter shifts or substitutions. For example, “chmu” could be a scrambled version of a common English word. Considering the entire phrase, we can look for patterns in letter frequencies and word lengths to aid decryption. Reversing the entire string, we get “rdwolw the taelvr ot ti si umhc ohw”. This immediately suggests a potential reversal of word order and potentially individual letters within each word.
Decryption Techniques
Several decryption methods can be applied to this cipher. The most straightforward approach is a trial-and-error method, systematically trying different letter substitutions or word rearrangements. More sophisticated techniques include frequency analysis (analyzing the frequency of letters in the ciphertext and comparing it to the known frequency of letters in the English language), and the use of known cipher algorithms. A Caesar cipher, for example, involves shifting each letter a certain number of positions down the alphabet.
Comparison of Decryption Techniques
| Technique | Steps | Potential Output | Feasibility |
|---|---|---|---|
| Reversal of Word Order | Reverse the order of words in the string. | “rdwolw the taelvr ot ti si umhc ohw” (initially yields a partially intelligible result) | High, easy to implement. |
| Letter Transposition | Attempt to rearrange letters within each word to form meaningful words. | Potentially reveals the original words once the correct letter shifts are determined. | Medium; requires systematic trial and error. |
| Caesar Cipher Analysis | Try different Caesar cipher shifts (1-25) to see if a meaningful phrase emerges. | A meaningful phrase if the correct shift is found. | Medium; computationally simple, but requires checking multiple shifts. |
| Frequency Analysis | Compare the frequency of letters in the ciphertext to the expected frequency in English. | Identification of likely letter substitutions. | Medium; requires some statistical knowledge. |
Conclusive Thoughts
Deciphering “who chmu si it to rvlaet eht lwodr” proves to be a complex yet rewarding endeavor. While multiple interpretations are possible, the process of analyzing the string highlights the importance of interdisciplinary approaches to problem-solving. By combining techniques from cryptography, linguistics, and contextual analysis, we can unravel the mysteries hidden within seemingly random sequences of characters. The ultimate meaning, however, remains dependent on the context and the intent of the original author – a reminder of the inherent ambiguity and potential for multiple valid interpretations in the world of coded messages.